Send passwords securely with Secure Password Share
As a software service provider, the topic of security is a natural companion in the planning and development of software. In everyday project work, however, it is unfortunately all too often forgotten - both on the service provider and customer side - that supposedly small things like "I'll send you the password via email." can have fatal consequences.
Secure Password Share is a new tool from doubleSlash for the secure and simple exchange of passwords. This article tells the story of how the tool came about and what makes it so special.

The doubleSlash innovation process
As a developer, I could no longer accept the existing problem of unencrypted password exchange in everyday project work - a solution had to be found. For this reason, I made use of our doubleSlash innovation process. The innovation process gives every employee the opportunity to contribute ideas for improving processes or products. These ideas are evaluated in a structured way and implemented if necessary.
While searching for a suitable tool, I came across many web apps that basically offered what I was looking for - a tool for exchanging passwords, but none of the tools I found could combine security and a good usability / user experience. That's why I suggested developing our own secure password exchange tool as part of the innovation process.
Safety must not give way to convenience
While IT security research is already looking into technologies such as quantum key exchange, the reality of everyday project work is that passwords are sent in plain text via email or chat. It is not just the lack of encryption that is the problem. Above all, the uncontrolled persistence of passwords in email and chat histories is a security risk that should not be underestimated. If you ask someone whether security is important to them, they will of course all answer "yes". The question is why security still gives way to convenience far too often (see the intention-behavior gap).
Of course, there are secure ways to send passwords, e.g. via PGP-encrypted emails. However, the problem of the initial PGP key exchange also exists here and is usually such a big hurdle that convenience wins out in the end and a password is sent in plain text. Even the best and most secure tool is useless if it is not used. That is why we have formulated our project goal as follows:
Secure Password Share
offers the best UX
for the secure exchange
of passwords.
To test the web app, we offer Secure Password Share to all employees at doubleSlash for the secure exchange of passwords with each other and with external partners/customers at this address: https://sps.doubleslash.de
Are you an external partner or customer of doubleSlash and would like to try Secure Password Share? Please ask your doubleSlash contact person for a Guest access link. If you want to use the secure Password Exchange tool directly for yourself and your company, you can purchase one of the packages on the Subscribe to Windows Azure Marketplace.
What can Secure Password Share do?
Send password
To send a password as an //employee to an external partner/customer, a password link must be generated after login. This can be done after entering the password by clicking on "Generate password link".
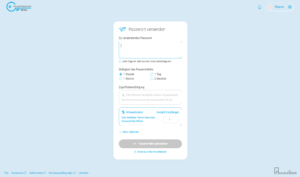
The generated password link can now be sent to the external partner/customer via a secure 1:1 channel.
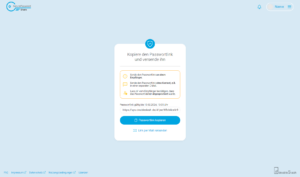
After calling up the password, the recipient first sees the following security information:
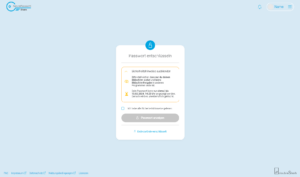
After clicking on "Show password", the password is decrypted and displayed.
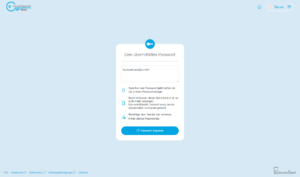
Request password
To request a password as an //employee from an external partner/customer, the //employee must generate a guest access link after logging in. This can also only be used once and for a limited time:
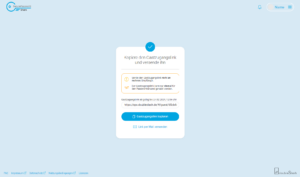
With this guest access link, the external partner/customer has one-time access to Secure Password Share to generate a password link. From here on, the process is similar to the Send password.
What makes Secure Password Share so secure?
The various security mechanisms prevent passwords from being stored uncontrolled and permanently in email or chat histories.
-
Secure end-to-end encryption
Encryption and decryption only take place locally in the browser. The required secret key is never sent to a server. Not even Secure Password Share itself can see the passwords.
More information on Wikipedia: End-to-end encryption. -
Your password can only be viewed once
As soon as a password has been decrypted or displayed, it is irrevocably deleted from the database.
-
Your password can only be viewed within a certain period of time
After a time selected by the sender, the encrypted password is irrevocably deleted from the database.
Even if the password link has been tapped by an attacker, the legitimate recipient will always be aware of this, as the following is displayed when the password link is called up in this case:
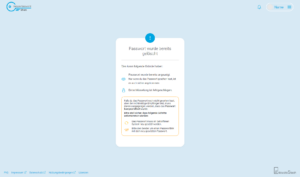
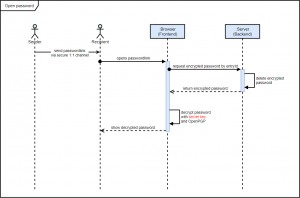
How does end-to-end encryption work in Secure Password Share?
The encryption process for generating the password link at the sender is shown in the following sequence diagram:
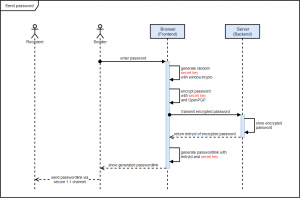
The decryption process for displaying the password to the recipient is shown in the following sequence diagram:
You can find more information at secure-password-share.com. Or discover the offer directly on the Microsoft Azure Marketplace.
If you have any questions or would like an individual offer, please do not hesitate to contact us.


In my opinion a very useful tool. Just like weTransfer! I will definitely be using it.